Posted by admin on January 20, 2017
The Basics of HIPAA Privacy and Security
The Health Insurance Portability and Accountability Act (HIPAA) mandates that covered entities comply with the HIPAA Privacy Rule, Security Rule and Breach Notification Standards set out by the Department of Health and Human Services (HHS) Office of Civil Rights (OCR). These covered entities include health plans, health care clearinghouses, health care providers who transmit health information in electronic form and business associates. Affectionately known as the “HIPAA Police,” this agency is responsible for protecting patients’ health information privacy rights.
The Privacy Rule dictates how protected health information (PHI) shall be used and disclosed. It strikes an appropriate balance of ensuring that patient information is maintained in a confidential manner while not hindering disclosures that would account for the treatment and payment of health care services.
The Security Rule has the same overall goal of protecting PHI with a specific focus on electronically created, maintained or transmitted PHI. Thus, the Security Rule protects electronic PHI (ePHI).
At a minimum, a covered health care entity is required to complete the following tasks to comply with the Privacy and Security Rules:
- Designate a Privacy Officer;
- Designate a Security Officer;
- Perform a Risk Analysis;
- Publish and Make Available a Notice of Privacy Practices;
- Adopt Policies and Procedures;
- Perform and Document Workforce Training;
- Develop and Implement Mitigation Procedures;
- Adhere to Administrative, Technical and Physical Safeguards of PHI;
- Adhere to Administrative, Technical and Physical Safeguards of ePHI;
- Develop and Implement Mechanisms to Receive and Handle Complaints and Breaches; and
- Perform Periodic Assessments and Audits
The HIPAA Breach Notification Rule specifically dictates how covered entities and their business associates must handle impermissible uses or disclosures of PHI, also known as breaches. This rule dictates the content of the notice, to whom notice must be given, timeliness of the notice and other appropriate deadlines. Breaches must be assessed to determine the number of individuals affected and the possibility of mitigation, both of which affect how the breach should be ultimately handled. For example, breaches affecting less than 500 people require individual notice, whereas breaches affecting 500 people or more require individual notice, notice to specific news outlets and notice to the Secretary of HHS. Due to the complexity of the breach notification standards, it is paramount that your privacy and security officers know and understand the breach notification requirements.
How much could non-compliance cost you?
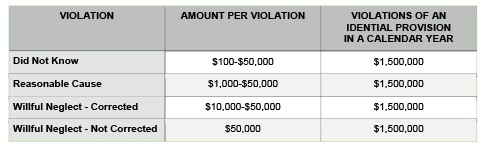
Not complying with HIPAA regulations can be expensive. The fines can range from $100 to $50,000 per violation, with a maximum of $1.5 million in a calendar year for repeat violations. The categories of violations are based upon the level of negligence demonstrated by the individual/entity that caused the breach. Penalties are based on the nature of the breach and the extent of harm caused by the breach.
The HHS Office of Civil rights has collected tens of millions of dollars in settlements. These settlement funds are then funneled back into the enforcement program to further strengthen their auditing efforts and oversight. This practice makes the program self-sustaining and will continue to grow and develop making it that much more likely that you or a health care provider that you know will be audited.
In August of 2016, Advocate Health Care Network settled with the HHS Office of Civil Rights for $5.5 million after it was determined that they failed to do the following:
- Conduct accurate and thorough risk assessments of ePHI;
- Implement policies and procedures to limit physical access to ePHI;
- Obtain business associate agreements assuring that business associates would appropriately safeguard PHI; and
- Safeguard an unencrypted laptop that was left in an unlocked vehicle overnight
In July of 2016, the University of Mississippi Medical Center reached a $2.75 million dollar settlement after numerous issues of non-compliance were discovered, including:
- Failure to implement policies procedures relating to security violations;
- Failure to implement physical safeguards of workstations that access ePHI and restrict access to authorized users;
- Failure to assign a unique name and/or number for identifying and tracking user identity in information systems containing ePHI; and
- Failure to notify individuals and follow breach notification standards after information was believed to be inappropriately accessed, acquired or disclosed.
Business associates were also fined, highlighting the importance of health care entities identifying their business associates and executing appropriate business associate agreements. In April of 2016, Raleigh Orthopedic Clinic, P.A. in North Carolina entered into a resolution agreement with a monetary payment of $750,000. It was determined that this entity turned over x-ray films and PHI to a company that would then harvest the silver from the x-ray films.
“HIPAA’s obligation on covered entities to obtain business associate agreements is more than a mere check-the-box paperwork exercise,” said Jocelyn Samuels, Director of the HHS Office of Civil Rights. “It is critical for entities to know to whom they are handing PHI and to obtain assurances that the information will be protected.”
On January 9, 2017, HHS announced a settlement with Presence Health for $475,000. This represented the first settlement based on the untimely reporting of breaches of unsecured PHI.
“Covered entities need to have a clear policy and procedures in place to respond to the Breach Notification Rule’s timeliness requirements,” said Director Samuels. “Individuals need prompt notice of a breach of their unsecured PHI so they can take action that could help mitigate any potential harm caused by the breach.”
Resolution agreements can go beyond requiring entities to pay fines. They may also require an entity to take specific corrective action and report their activities to HHS Office of Civil Rights for a designated time. Often this probationary period lasts from one to three years. Additional information on fines and resolution agreements are available on the OCR website.
In addition to steep fines, an equally threatening issue is damage to your reputation. There is no doubt that media coverage of publicized breaches can have a chilling effect on patients who are already on heightened alert to issues like identity theft. Last year alone, OCR publicized settlements ranging from $25,000 to $5.5 million. They also maintain a scrolling section on their web page, affectionately known to compliance professionals as the “Wall of Shame.”
Should your organization receive the unpleasant honor of being highlighted on this website, you should know that it details information on the underlying offense and OCR has no intention of removing past offenders, regardless of how long ago their misdeeds occurred. A quick glance at the Wall of Shame contains breach information on over 1,798 separate incidents dating all the way back to 2009. https://ocrportal.hhs.gov/ocr/breach/breach_report.jsf
The covered entities hit the hardest by enforcement action are listed below based on frequency:
- Private Practices
- General Hospitals
- Outpatient Facilities
- Pharmacies; and
- Health Plans
According to OCR, issues investigated most are, compiled cumulatively, in order of frequency:
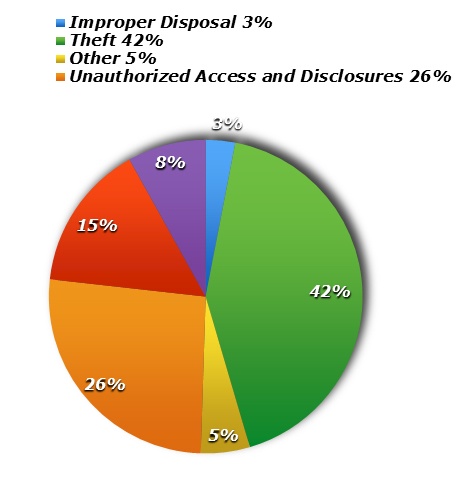
- Impermissible uses and disclosures of PHI;
- Lack of safeguards of PHI;
- Lack of patient access to their PHI;
- Lack of administrative safeguards of electronic PHI; and
- Use or disclosure of more than the minimum necessary PHI
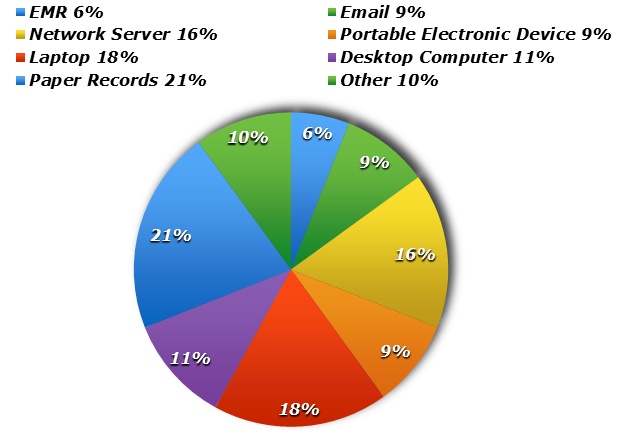
But where might health care entities be most vulnerable? According to Jerome Meites, a Chief Regional Counsel for the Office of Civil Rights, “Portable media is the bane of existence for covered entities. It causes an enormous number of the complaints that OCR deals with.” Portable media includes laptops, cellphones, hard drives and flashdrives. While these instruments are vital to communicating information in the health care setting, the amount of data contained on these devices makes their security a primary focus for Privacy and Security Officers.
Threats to medical practices and other covered entities exist and the consequences of enforcement actions and private litigation can be devastating. Covered entities must address these issues on the front end. Covered entities should assess the strengths and weaknesses of their compliance programs to protect themselves and their patients.
Samarria Dunson (samarria@dunsongroup.com) is attorney/principal of Dunson Group, LLC, a health care compliance consulting and law firm in Montgomery, Alabama. www.dunsongroup.com
Tags: HIPAA
Posted in: HIPAA