Posted by admin on January 3, 2017
With the increased use of technology in health care comes the increased risk of cyber attacks and cyber liability, as well as regulatory investigations, fines and penalties. Anything created, stored or transmitted electronically is at risk of being compromised by an innocent mistake or – worse yet – maliciously stolen by a criminal.
According to a compilation of data breach statistics, there were 1,673 reported data security breach incidents worldwide in 2015, and 1,222 of those occurred in the United States. Of that total, 374 – approximately 22 percent – were breaches of medical or health care information. This equated to more than 134 million individual health care data records being accessed or stolen by cyberattacks just in calendar year 2015 alone.1
Many people don’t believe — or understand why — medical information is valuable or at risk.
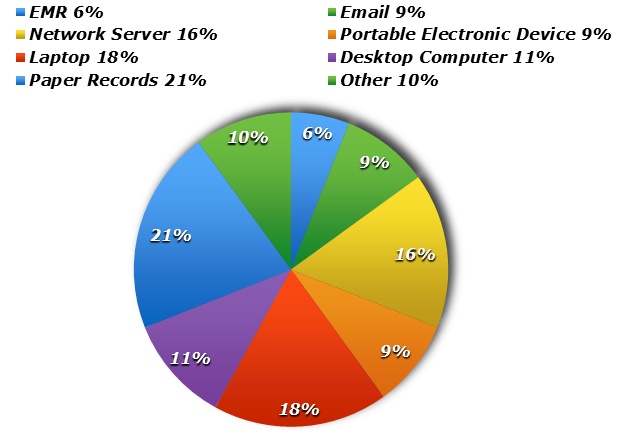
Medical records are targeted because they contain a wide variety of a patient’s personal information: social security number, financial, health, demographic and family information. This gives criminals many potential uses for the stolen information, including identity theft and applying for credit cards, store accounts, or other lines of credit. But they also use the information to purchase medical equipment and pharmaceuticals that can be resold, or to fraudulently bill health insurers or the government for fictitious medical care by masquerading as health care providers. One cybersecurity expert estimates that a medical record can fetch up to $50 on the black market, while a credit card number may go for as little as $5.2
Big or small, all health care organizations are at risk.
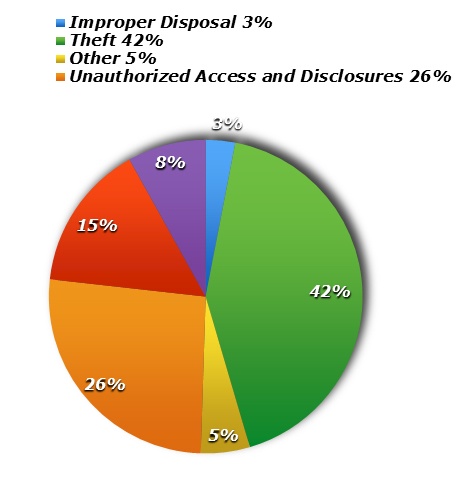
Large health care systems, hospitals, group practices and individual health care providers have all been attacked, but the size of the entity is no clear indication of the size of the breach. One need only reference the HIPAA data breach “wall of shame” to bear out the truth of this assertion. Data breach incidents at very large organizations have exposed anywhere from several hundred to several million patient records. Likewise, cyber attacks on small solo practices — though frequently in the range of several hundred to several thousand — have exposed tens of thousands of patient records with a single breach.
Transition to EHRs, dated systems, and weak security measures pave the way for cyberattacks.
The transition to electronic health records has given criminal hackers more opportunities to steal medical records. The chief information officer for a hospital system in Utah estimates his hospital’s EHR system fends off thousands of attempts to penetrate its network each week.3
Another reason is ease of access. Many hospitals and physician practices are using EHR systems that have not been updated in more than 10 years. While hospitals and physician practices grappled with more urgent matters like ICD-10 implementation and Meaningful Use, robust cybersecurity measures fell down the priority list. Once a hacker penetrates whatever security the system does have, the exposed information is there for the taking.4
Cyberattacks on EHR systems take many forms.
In addition to outright theft of medical information, emerging cyber threats also include various forms of cyber terrorism and cyber extortion. Recent reports of ransomware attacks are particularly troublesome. Sophisticated hackers launch malicious codes (typically via entry through email) that crawl through a target’s computer system, encrypting and locking up data files, and then demand payment (ransom) in exchange for providing the decryption key. Cybersecurity experts believe health care providers make good targets for ransomware attacks because they do not typically have the advanced backup systems and other resilience measures in place that are typical of other types of organizations.5
What can you do to safeguard EHRs and protect patient information?
Patient trust in your practice’s ability to protect medical information is critical. To maintain that trust, it is important to have safeguards in place that help prevent data breaches. When implementing or updating an EHR system for your practice, talk to your vendor about cybersecurity. Ask whether the stored information is encrypted. It is also a good idea to determine if or when the vendor will provide security updates for your EHR software.
You may need to invest more resources in shoring up the walls around your electronically stored and transmitted data. Cybersecurity is a highly specialized area that requires a certain degree of expertise and experience. Your EHR vendor may be able to provide some assistance in this area, but remember their expertise is more about creation and functionality and less about security. Hiring an in-house cybersecurity expert or contracting with a cybersecurity firm specializing in this area may be the best option to protect your practice and your patients.
ProAssurance also helps protect you against cyber liability threats.
ProAssurance is also committed to helping you reduce uncertainty and increase the control you have over cybersecurity — it’s only fair. That’s why we partnered with NAS Insurance Services to provide coverage for certain types of cyber liability risk exposures. This coverage, called CyberAssurance Plus®, is now embedded in your existing ProAssurance professional liability insurance policy and is provided at no cost to you. Through CyberAssurance Plus® you have coverage for Network Asset Protection, Privacy Breach Response Costs and Patient Notification Expenses, Patient Support and Credit Monitoring Expenses, Privacy and Security Liability, as well as coverage for Regulatory Defense Costs and certain Fines and Penalties. This embedded coverage was recently enhanced to also include coverage for Multimedia Liability, Cyber Extortion and Cyber Terrorism, PCI DSS Assessments, and a unique coverage feature called BrandGuard® for lost revenue as a result of an adverse media report or customer notification of a security or privacy breach. Your CyberAssurance Plus® coverage is limited to $50,000 per claim and subject to an annual aggregate limit (determined by group size) for all claims in a single policy year. You may, however, purchase higher coverage limits for cyber liability threats through ProSecure®, which is a co-branded insurance program with NAS Insurance Services that is exclusive to ProAssurance insureds. Through ProSecure® you can purchase an additional $1 million in cyber liability coverage that is designed to work seamlessly with CyberAssurance Plus® coverage already embedded in your ProAssurance policy.
As a ProAssurance insured, you and your staff also have access to webinars, toolkits, bulletins, posters, FAQs, and online training programs to help you address cyber liability risks. For example, you can access:
- Summaries of major changes to the HIPAA/HITECH Rules (effective September 2013), including required changes to your Notice of Privacy Practices; the expanded definition of Business Associates (with updated sample Business Associate and Vendor Agreements); and patients’ ability to request medical records in electronic form
- Webinars, tool kits, and sample documents, including basic data privacy/security, encryption, and destruction practices; sample HIPAA Privacy/Security Rule policies and procedures; social media training tools; sample mobile and personal device user policies, procedures, and agreements; and how to implement a data security plan
- Breach notification requirements under federal and state laws (where applicable); sample HIPAA Breach/Risk Assessment Worksheets; examples of incidents to report, how to report data security incidents, and more
You can access these resources from NAS Insurance Services’ Data Security Risk Resource Website through your proassurance.com account. Please Note: Content on the NAS Insurance Services’ Data Security Risk Resource Website is provided by third party sources. ProAssurance is not responsible for the content and does not consider it to be legal advice.
For more information about cyber liability, cybersecurity, risk management, CyberAssurance Plus® and ProSecure®, contact your ProAssurance representative. Article by ProAssurance, a Platinum Partner with the Association. ProAssurance insured physicians and their practice managers may contact Risk Resource for prompt answers to liability questions by calling (844) 223-9648 or email riskadvisor@proassurance.com.
SOURCES
1 2015 The Year Data Breaches Got Personal: Findings from the 2015 Breach Level Index. Gemalto website. http://www.gemalto.com/press/Pages/Gemalto-releases-findings-of-2015-Breach-Level-Index.aspx. February 23, 2016. Accessed September 8, 2016.
2 Murphy T., Bailey B. Hackers mine for gold in medical records. The Boston Globe website. https://www.bostonglobe.com/business/2015/02/06/why-hackers-are-targeting-medical-sector/xxjFN6G3cFJZ8Fh3mF3XhN/story.html. February 6, 2015. Accessed September 1, 2016.
3 Humer C., Finkle J. Your medical record is worth more to hackers than your credit card. Reuters website. http://www.reuters.com/article/2014/09/24/us-cybersecurity-hospitals-idUSKCN0HJ21I20140924. September 24, 2014. Accessed September 1, 2016.
4 Radcliffe S. Patients beware: hackers are targeting your medical information. Healthline News website. http://www.healthline.com/health-news/hackers-are-targeting-your-medical-information-010715#1. January 7, 2015. Accessed September 1, 2016.
5 Conn J. Hospital pays hackers $17,000 to unlock EHRs frozen in ‘ransomware’ attack. Modern Healthcare website. http://www.modernhealthcare.com/article/20160217/NEWS/160219920. February 18, 2016. Accessed September 1, 2016.





 ributed by Nic Cofield, Jackson Thornton Technologies Consultant. Jackson Thornton is a Certified Public Accounting and Consulting Firm and an official partner with the Medical Association.
ributed by Nic Cofield, Jackson Thornton Technologies Consultant. Jackson Thornton is a Certified Public Accounting and Consulting Firm and an official partner with the Medical Association.