What’s the Biggest Threat to Your Medical Practice? Your Staff!

Many of us are aware of recent attacks impacting health care entities large and small. As ransomware and other cybersecurity-related crimes are being reported daily, there is a tremendous focus on the “dark web” and how to decrease the likelihood your entity will be impacted by hackers. But as we put systems in place to deal with those security issues, we must not forget about the threat of other malicious actors. These individuals are not strangers who only interact with our computer systems remotely. This threat is much closer. We’re referring to your staff members who may inappropriately access and utilize patient data for personal gain.
Employers generally believe they hire the best candidates. In most instances that is correct. After combing over résumés and doing countless interviews, it is determined the selected individual is a person you can trust and respect. As these individuals prove themselves to be competent and dependable, many of us will place a high level of confidence not only in that person’s ability to perform the job, but also in their character.
As time passes we learn a lot about our colleagues. We learn about each other’s families, interests and life goals. We become invested in our co-workers, and we share in moments of success and disappointment. These events endear us to one another and become the fabric of our working relationships. However, just as this bonding is reflective of our human desire to find commonalities, these relationships can also blind us to a very serious threat. This threat is the impact that these very individuals can have on our entities if they intentionally or inadvertently compromise a patient’s protected health information (PHI). We must constantly remind ourselves good people can do bad things depending on that individual’s circumstances at the time they make a compromising decision.
“Insider threat” is a term used to describe the threat to an entity’s systems or data that originates from within the entity. These “insiders” can be current or former employees, contractors, or business associates who have or has had authorized access to an entity’s systems or data and misuse that access.
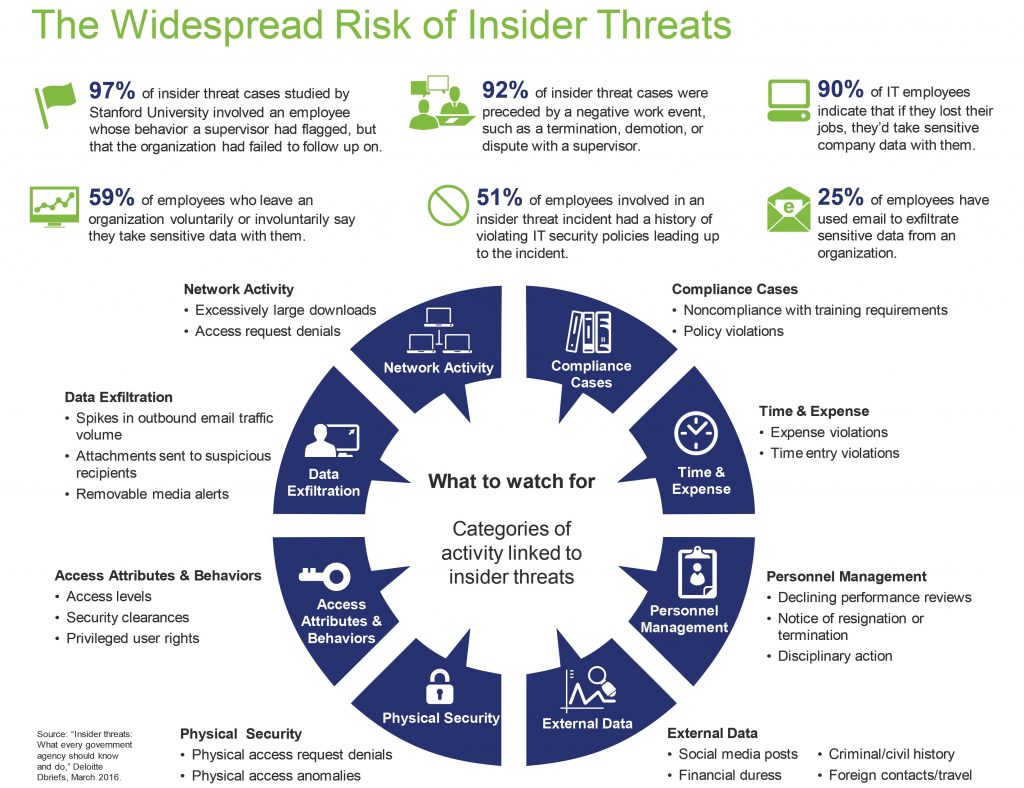
Red Flag Behavioral Indicators
When entities endure a significant data breach, they are often in disbelief the incident occurred. Then as they begin the investigation phase, they realize there were behaviors exhibited by the bad actor that should have drawn suspicion.
Here are some behaviors entities should be watchful of:1
- Works odd hours without authorization; notable enthusiasm for overtime work, weekend work, or unusual schedules which may result in them being able to carry out their illicit activities privately.
- Remotely accesses the computer network while on vacation, sick leave, or at other odd times.
- Interest in matters outside the scope of their duties, particularly where patient data may be stored and how that information may be accessed.
- Unexplained affluence; buys things they cannot afford on their household income.
- Without need or authorization, takes proprietary or other material like patient information home, via paper records, thumb drives or by emailing information to their personal email accounts.
- Overwhelmed by life crisis or career disappointments.
- Paranoia about being investigated; believes there are listening devices or cameras in their homes or workplaces.
- Disregarding computer policies on installing personal software or hardware, accessing restricted websites, conducting unauthorized searches, or downloading confidential information.
How to Reduce Your Risk
- Appropriately manage your employees. Entities should pay particular attention to individuals who are disgruntled or who may be undergoing financial hardship. Also, be watchful of employees who show up to work very early or leave very late with no work product to show for the extra time they’ve worked. Additionally, background checks can be very telling. This is especially true for employees whose records identify financial issues like issuing bad checks.
- Be mindful of security access privilege designations. Only provide employees with the security access privileges they need to perform their job functions. The less access they have to patient data that does not involve them, the less likely they will be able to create large data breaches.
- Proactively audit user access. Perform audits of user actions to determine who has been remoting into your entity’s computer network or who has been accessing your systems after normal business hours. Review reports of failed log-in attempts to determine whether employees are trying to log into systems they have not been officially granted access to view.
- Develop and adhere to effective termination procedures. Once you become aware an employee will need to be terminated, make plans to disable their physical and system access such that the terminated employee does not have the opportunity to negatively impact your entity or systems. During the exit interview, make it clear to the terminated employee your entity will not tolerate inappropriate data access and will seek criminal prosecution if it discovers any employees are engaging in such activity.
- Effective training programs. Ensure your employees are aware of your entity’s privacy and security policies and procedures. Reiterate these principals in training and inform them of the consequences of not adhering to these requirements. Additionally, train employees to be particularly watchful of co-workers who exhibit the behavioral indicators described above. Ensure they know the warning signs and to whom to report their concerns.
- All insiders are not necessarily in your building. Be mindful that Business Associates and contractors may also have access to your systems
and data. The activities of these users should be monitored as well. Individuals within those entities should be signing confidentiality agreements at a minimum and Business Associate Agreements, when applicable.
Your entity’s designated Security Officer can play a key role in monitoring the electronic behavior of staff members, Business Associates and contractors. Ensure this individual is knowledgeable about your entity’s HIPAA security policies and procedures, and they are following up on audits that identify behaviors that may be placing your patient data at risk. If your entity does not have updated HIPAA security policies and procedures, consider hiring a health care compliance professional to ensure regulatory compliance.
Article contributed by Samarria Dunson, J.D., CHC, CHPC, attorney/principal of Dunson Group, LLC, a health care compliance consulting and law firm in Montgomery, Ala.
References
1 “The Insider Threat”, U.S. Department of Justice Federal Bureau of Investigation; https://www.fbi.gov/file-repository/insider_threat_brochure.pdf
2 “Insider Threats: What every government agency should know and do,” Deloitte Dbriefs, March 2016.
Posted in: HIPAA
Leave a Comment (0) ↓