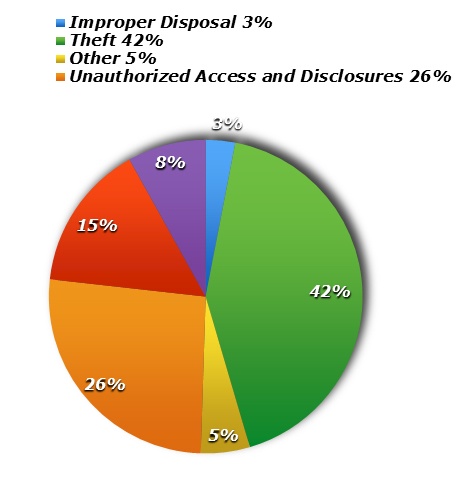
A HIPAA breach often occurs when a health care entity wrongfully discloses the protected health information of a patient or client. These incidents can occur by accident, like faxing patient information to the wrong fax number. They can also be the result of willful or intentional acts, like employees who gather patient information for the purpose of filing false tax returns. They occur in many forms and can affect any number of individuals. Breaches can range in scale from a single individual being compromised to an incident affecting thousands and even millions of people.
The Department of Health and Human Services requires a breaching entity to take specific reporting action based on the number of individuals the breach affects. In the world of HIPAA breaches, 500 is a magic number. Breaches affecting greater than 500 individuals are generally considered a HIPAA “Mega” breach. These mega beaches have more stringent notification requirements that could cause your health care practice to be featured on the evening news. Just as with breaches affecting fewer than 500 people, mega breaches require that you provide individual notice to each patient. This often requires staff time as they work to locate each patient’s last known address and send them a breach notification letter explaining what happened, who was involved, how their data was compromised, and what the entity is doing to avoid similar incidents in the future. Often, entities will offer their patients credit monitoring for a two-year period to mitigate the breach and demonstrate to the patient that the entity is serious about data security.
Mega breaches also require individual notice. However, these large breaches also require simultaneous notice directly to the HHS Office of Civil Rights and local media and news outlets. Entities reporting these large breaches will deal with immediate issues like loss of business and loss of reputation while also responding to patients and clients who are angry that their information has been compromised.
How can you avoid dealing with a HIPAA Mega breach in your practice?
You Must Perform a Competent and Thorough Risk Analysis. Many compliance professionals refer to this as your entity’s “annual exam.” During this process, you and your team should determine every system that contains electronic protected health information and assess its vulnerability for inappropriate disclosure. This analysis is a requirement of the HIPAA Security Rule and must occur annually or sooner if necessitated by changes to your IT system or turnover in your workforce. Entities must remember to document this process and have it readily available to produce to HHS upon request. Failure to perform, document, and/or produce an adequate Risk Analysis is often a sign to HHS that an entity is non-compliant and may lead to a more extensive audit. This is an opportunity for entities to determine the adequacy of their cybersecurity and how to protect their entity from malware.
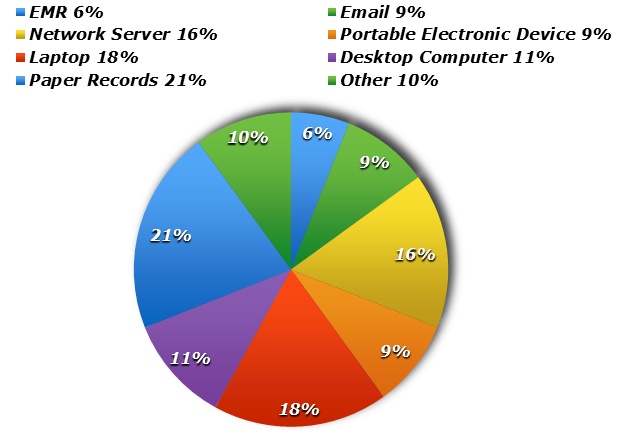
Invest in Encryption. HIPAA categorizes patient data in two ways: (1) secured and (2) unsecured. Entities most often find themselves in trouble when they have a breach of unsecured The breach notification requirements discussed above which include notice to patients, HHS and media outlets ONLY refer to breaches of unsecured data. However, secured data is exempt from notice requirements. Secured or encrypted data is considered to be unusable, unreadable, or indecipherable to unauthorized individuals; thus, a breach of that device cannot occur. Encrypting patient data is the ultimate safety net! For example, a nurse uses a business laptop to store patient information of the 550+ individuals that are treated in her practice. She takes it home for the night and leaves it on the passenger seat of her car. Her vehicle is broken into overnight and the laptop is stolen. If the laptop is unencrypted, she now faces HIPAA breach notification requirements, loss of reputation, and the overwhelming threat of possible fines and lawsuits. However, if the laptop is encrypted, she would simply document the occurrence and have the laptop replaced.
Enforce Privacy and Security Policies and Provide Training. Often, the most effective tool in your health care compliance arsenal is a competent and well-informed workforce. Employees must understand how their actions can affect the security of data along with the consequences of violating policies and procedures. Additionally, having policies and procedures that are customized to your practice demonstrates a serious approach to compliance. Often, being able to produce copies of polices and training that employees were mandated to review and participate in will reflect that the entity itself was aware of its risks and sought to avoid or minimize them. An employee who has documented that they have reviewed the policies and participated in training, but nevertheless participated in negligent or reckless behavior, is more likely to be seen as a “bad actor” and not a reflection of a culture of non-compliance within the entity.
You’re entity may also want to reflect on how the following devices are utilized and stored:
- Hard Drives
- CDs/DVDs
- Flash Drives
- Back-Up Storage Tapes
To ensure that your practice is complying with federal regulations, and for assistance with avoiding or navigating a mega breach, please consult a health care compliance professional.
Samarria Dunson, J.D., CHC, CHPC is attorney/principal of Dunson Group, LLC, a health care compliance consulting and law firm in Montgomery, Alabama. www.dunsongroup.com
